Shift Left Security: Prevent Breaches, Preemptively
Automatically scan your IaC after every change, directly on Git, to prevent misconfigurations from turning into breaches. Stop security incidents at the source and protect your cloud from the outset.
Identity-Centric Security: Secure Every Change
Track every identity-driven change across your cloud, instantly detecting misconfigurations from IaC to live resources. Eliminate blind spots and minimize risk by securing your most critical perimeter: Identity.

Automated Governance: Stay Compliant, Effortlessly
Enforce industry regulations and internal security policies, eliminating manual policy checks and ensuring consistent compliance. Free your team to focus on strategic initiatives while maintaining continuous compliance and a robust security posture.

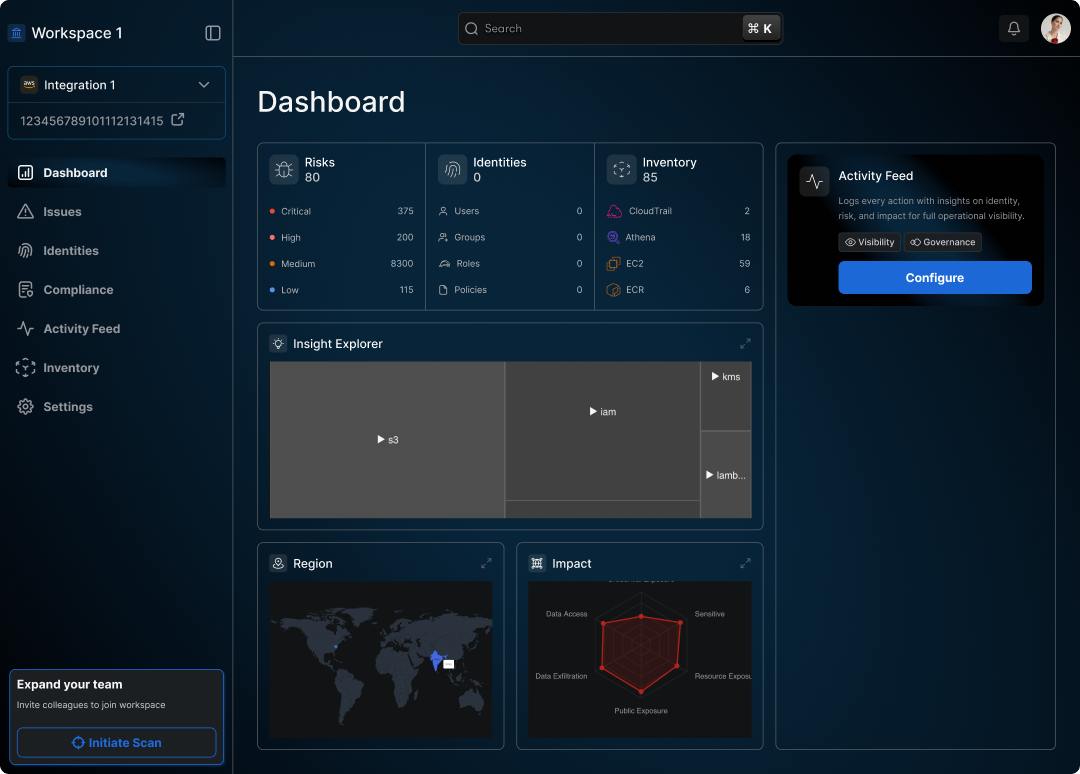
Unified Risk View: Act on Insights, Faster
Gain a holistic view of risks across all identities (human and non-human), activities, and cloud resources. Rapidly identify and prioritize risks, and leverage intelligent analytics for actionable insights that drive faster security responses.